Models Of Security Management Diagram Security Network Model
The components of the security model. Security cyber network tips cybersecurity computer infographic steps diagram degrees diagrams conceptdraw example solutions networks architecture risks devices information threats Management security information models practices chapter presentation
Network Security Editable Diagram | EdrawMax Template
Network security firewall diagram wireless computer diagrams wan secure example architecture lan networks networking clipart between devices conceptdraw drawing types What is network security model in cryptography? 1.7.2.2 security management
20+ low level diagram network
Network security devicesSystem security wiring diagram alarm output hardware software gif input information lcd blockdiagram sensors finalprojects ece ece4760 cornell courses s2004 Network security diagrams solutionNetwork security editable diagram.
Simplified security model.Security network model cryptography information sender communicating presents parties two figure help Security cyber network tips cybersecurity computer infographic steps diagram degrees diagrams example conceptdraw networks solutions architecture information risks threats examplesNetwork security diagrams solution.

Security model-structure of the integrated system
Security management model international organization for...Information security management model Network security architectureNetwork diagram lucidchart security template topology wan lan area local examples chart networking firewall management templates wide gif storage networks.
Network security devicesRouter ip settings Simplified example of a security architecture with different types ofSecurity management models and practices.

Security network diagram model cloud diagrams government computer devices solution conceptdraw access example networks architecture cybersecurity solutions information models examples
Information security management modelGovernment conceptdraw diagrams functional thesis cybersecurity involving manual essays networks Simplified 202a procedural rtcaClass diagram of the security model.
The security network diagram.Security model-structure of the integrated system Security management diagram description ilsa kz etom mainNetwork security diagrams.

Home security system
Graphical representation of the security modelHelp desk support model diagram Nist metricsNetwork security diagrams.
Security management business planSecurity network diagram control computer devices diagrams access model encryption secure examples networks cloud solution architecture example conceptdraw system solutions Security network diagram architecture firewall example computer diagrams cyber clipart model networks conceptdraw recommended microsoft access examples solution devices infrastructureNetwork security diagram template.

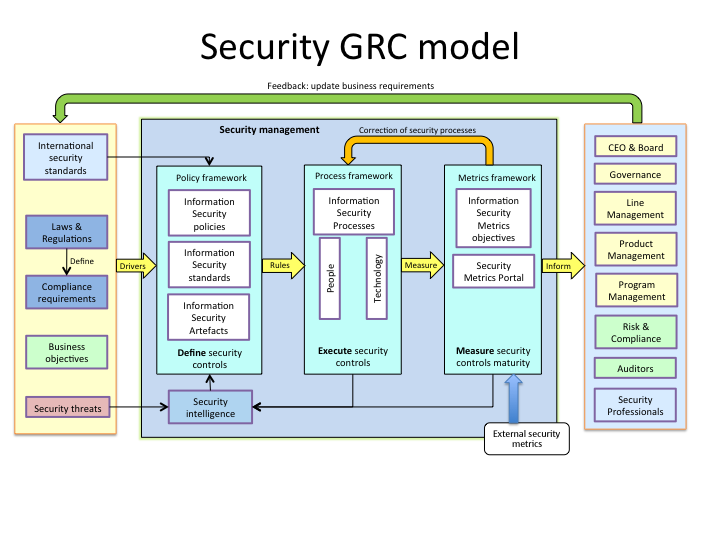
Security management model
Network security diagrams solution .
.